Technology
Technology
The Battle of the Hard Drives: Refurbished vs. New!
In today’s digital age, the need for reliable data storage solutions has never been greater. Whether for personal use, enterprise-level operations, or anything in between, the choice of hard drives is critical. Traditionally, new hard drives have been the go-to for ensuring top-notch performance and reliability. However, the rise of refurbished hard drives has challenged this norm, offering compelling benefits that are both budget-friendly and eco-friendly.
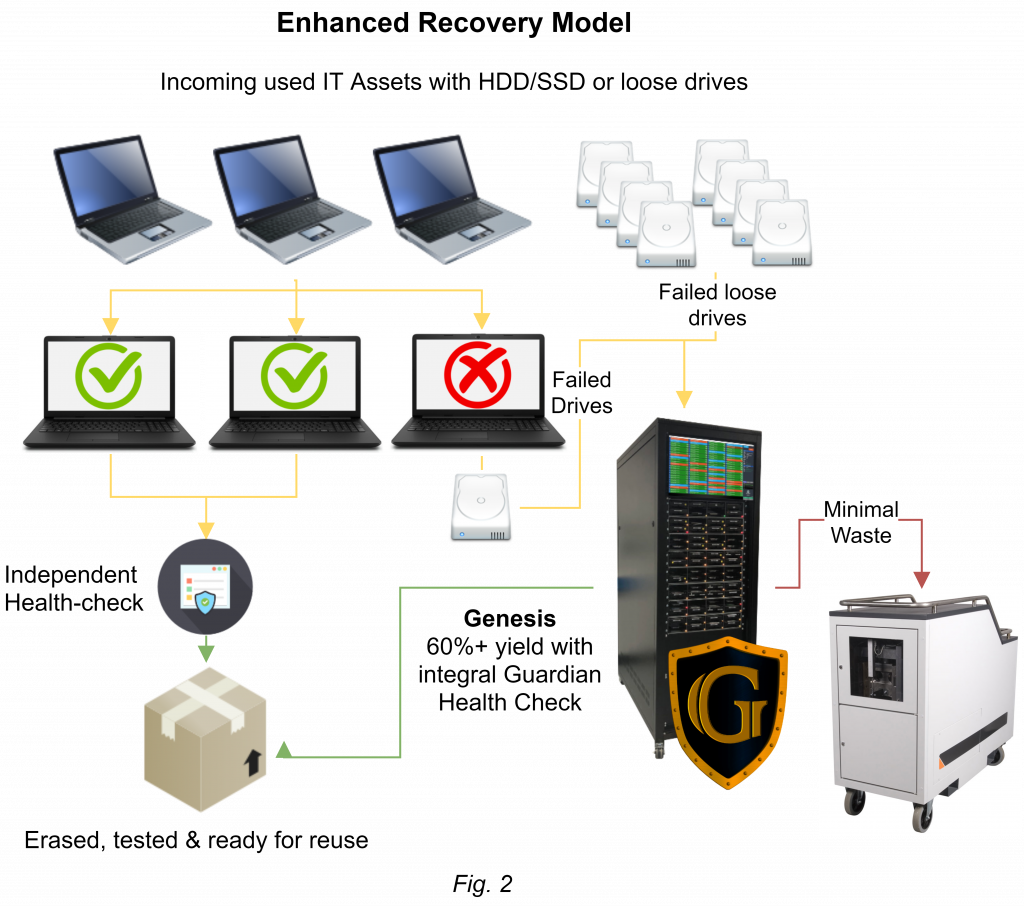
At the forefront of this revolution is the Ultratest Genesis, a leading solution for the refurbishment and regeneration of hard drives. Let’s delve into the advantages and drawbacks of refurbished drives compared to new ones and why opting for refurbished might be the smarter choice.
Why Choose Refurbished Hard Drives?
Budget-Friendly
One of the most significant advantages of refurbished hard drives is cost efficiency. New hard drives can be expensive, especially when considering high-capacity models or enterprise-grade units. Refurbished drives, on the other hand, are typically priced much lower. This makes them an attractive option for individuals and businesses looking to maximise their budget without sacrificing quality.
Eco-Friendly
Environmental sustainability is a growing concern, and the tech industry is no exception. Manufacturing new hard drives involves mining raw materials, consuming energy, and generating electronic waste. By choosing refurbished hard drives, you’re actively reducing your carbon footprint. Refurbishment extends the lifecycle of existing hardware, meaning fewer drives end up in landfills and less demand for new resources.
Certified Data Erasure
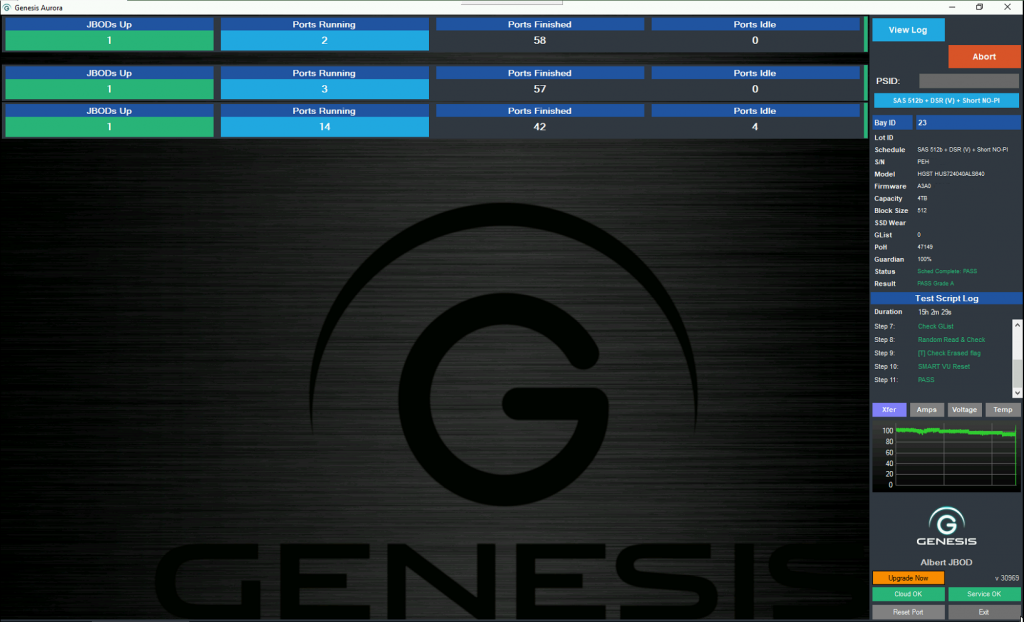
A major concern with refurbished hard drives is data security. The Ultratest Genesis addresses this with full-certified data erasure, ensuring that all previous data is completely and securely wiped. This guarantees that refurbished drives are not only free from previous data but are also compliant with stringent data protection regulations.
Grade A Condition
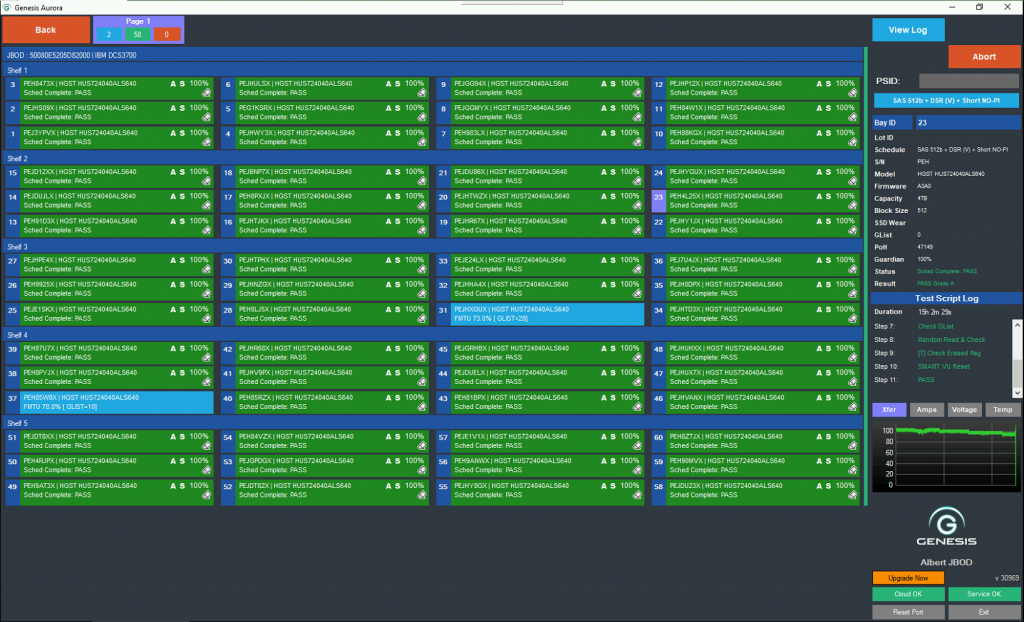
Refurbished does not mean subpar. Drives processed through Genesis undergo thorough testing and repair, ensuring they meet Grade A condition standards. This means they perform at levels comparable to new drives, offering reliability and efficiency for all your storage needs.
Pros and Cons of Refurbished Hard Drives
The Pros:
- Cost Savings: Significantly cheaper than new drives, allowing for better allocation of resources.
- Environmental Impact: Reduces electronic waste and resource consumption, contributing to a greener planet.
- Certified Data Security: Full data erasure ensures previous data is irretrievable, maintaining security standards.
- High Performance: Refurbished to Grade A condition, guaranteeing reliable performance.
- Availability: It is easier to find older models that might not be available new, useful for legacy systems.
The Cons:
- Perceived Reliability: Some may view refurbished drives as less reliable, though this is mitigated by rigorous testing and repair.
- Warranty Limitations: Refurbished drives often come with shorter warranties compared to new drives.
- Availability: Stock can be limited and inconsistent, depending on the supply of drives for refurbishment.
- Technological Advancements: Newer drives may offer the latest technology and higher capacities that refurbished ones might not match.
Conclusion
In the battle of refurbished versus new hard drives, it’s clear that refurbished drives offer substantial advantages in terms of cost savings and environmental impact. With solutions like the Ultratest Genesis, which ensures certified data erasure and Grade A condition refurbishment, the perceived risks of opting for refurbished drives are significantly minimised. For budget-conscious and eco-friendly consumers, refurbished hard drives present a compelling alternative that does not compromise performance or reliability. Embrace the future of sustainable technology with confidence, knowing that refurbished drives from Genesis are a smart, secure, and sustainable choice.