Product Update
Product Update
Securing the Network: The Imperative of Data Erasure in…
In the complex landscape of IT asset disposal (ITAD), securing data on retired network equipment such as routers, switches, firewalls, and access points is a critical yet often overlooked aspect of cybersecurity. Ultratest, a pioneering designer and manufacturer of integrated hardware/software solutions for data erasure, testing, and repair, shines a light on this pivotal issue. Their insights not only highlight the risks associated with inadequate data sanitisation practices but also introduce a groundbreaking solution that addresses these challenges head-on. Securing the Network: The Imperative of Data Erasure in IT Asset Disposal.
The Hidden Risks of Inadequate Data Sanitisation
As organisations upgrade their network infrastructure, the proper sanitisation of retired assets is frequently underestimated. This oversight can lead to severe data breaches, putting sensitive information at risk of unauthorised access. The reality is that simply deleting files or formatting devices does not erase data beyond recovery. Sophisticated techniques can still retrieve this information, posing a significant threat to data security.
Moreover, the challenge of data erasure is compounded by the necessity to preserve the inherent value of the network equipment. Often, the process of erasing data can inadvertently remove licences and operating systems, rendering the devices virtually useless. This not only diminishes the resale value of the assets but also contravenes the principles of sustainable ITAD practices by promoting unnecessary waste.
Legislative Compliance and Asset Value Retention
Adherence to stringent data destruction standards, such as NIST 800-88, is not just a matter of best practice but a legal imperative. These guidelines ensure that data is irrecoverably erased, safeguarding against potential breaches. However, achieving compliance while retaining the residual value of IT assets poses a unique challenge. The erasure process must be meticulous enough to protect sensitive information while preserving the device’s licences and operating systems – essential components that significantly contribute to the asset’s market value. Learn more about NIST here.
Furthermore, with the increasing focus on corporate responsibility and environmental sustainability, the Asset Disposal and Information Security Alliance (ADISA) certification has become a hallmark of excellence in the ITAD sector. This certification guarantees that the erasure processes not only meet but exceed the highest standards of data security and environmental stewardship.

Ultratest’s Nemesis: The Ultimate Solution
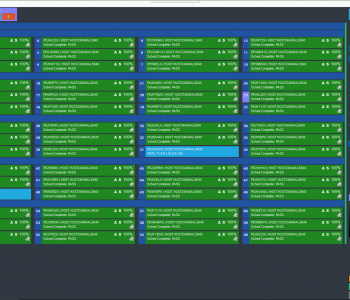
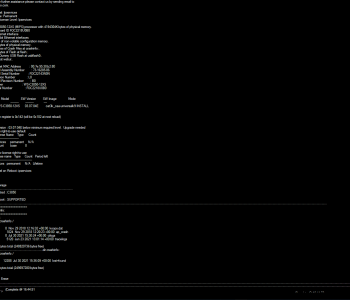
Enter Ultratest’s Nemesis, a comprehensive solution designed to address the multifaceted challenges of network equipment data erasure. Nemesis stands out as a versatile tool that ensures the secure, compliant, and efficient erasure of data from routers, switches, firewalls, and access points. What sets Nemesis apart is its ability to meticulously erase sensitive data while preserving the device’s licences and operating systems, thus maintaining the asset’s value.
Nemesis is engineered to be deployed directly within ITAD facilities, regardless of their location. This flexibility ensures that the erasure process can be seamlessly integrated into existing workflows, providing ITAD professionals with a reliable tool that not only complies with NIST 800-88 guidelines but also boasts ADISA certification. With Nemesis, organisations can rest assured that their retired network equipment is sanitised to the highest standards, mitigating the risk of data breaches and contributing to a more sustainable IT ecosystem.
Additionally, Ultratest’s Nemesis stands out for its plug-and-play capability, embodying a de-skilled approach to data erasure. This feature allows ITAD facilities to efficiently process equipment without extensive technical knowledge, simplifying operations and minimising the potential for human error. The intuitive design of Nemesis ensures a foolproof and efficient data sanitisation process, making it an essential, user-friendly tool in IT asset disposition.
Conclusion
The secure disposal of IT assets, especially network equipment, is a critical component of modern cybersecurity strategies. Ultratest’s Nemesis product addresses the pressing need for a solution that ensures data is erased securely and compliantly without compromising the residual value of the asset. By adopting Nemesis, ITAD facilities can offer their clients peace of mind, knowing that their retired assets are handled with the utmost care, security, and efficiency. Ultratest not only sets a new standard in data erasure solutions but also champions the cause of sustainable ITAD practices, ensuring that security and value retention go hand in hand. Learn more about Nemesis here.
Securing the Network: The Imperative of Data Erasure in IT Asset Disposal