 Technology
Technology
ITAD’S, ARE YOU SURE YOU’RE PROCESSING YOUR NETWORK PRODUCTS…
Written By Adam Burrett (Network Engineer, Nemesis Designer)
Introduction
When networking hardware is in use, network engineers are conscious to make sure they can always get back to a working configuration without having to redo the whole thing. Especially if it is remote.
So they tend to make a backup of the running / start-up config onto flash (I know, I used to). They may also carry out packet traces on the device, and store these in the flash and not delete it once finished. If this is a device that carries voice traffic that could include voice calls. With the right knowledge, you can download that file and listen to the call.
When that device becomes end of life the following need to happen:
- The startup configuration is erased
- Any backup configs are erased
- Any traces are erased
- Any file, that is not an operating system, is erased
You will notice that I have bolded the word erased. This is because erased data is not the same thing as deleted data.
If you delete a file from flash, you have not deleted it. You have removed the pointers to that file, and marked it to be overwritten when more storage is needed.
Flash tends to only allow you the option to format to totally clear it. This again, does not delete any of the data.
This data can be recovered using the right tools, in some instances just a compact flash card reader and a Hex editor.
The challenges
Maintaining Value
The main problem when processing networking equipment is that there are so many different types, each with their own unique processing method and varying levels of erasure commands.
The second major problem is maintaining the value of the asset. One wrong command and you can turn a £2000 switch into a £200 switch, or a piece of scrap.
A large number of ITAD companies currently sell their networking devices in bulk to upstream vendors for a much reduced value, potentially losing thousands of pounds on each batch they sell.
Complete Data Erasure
To date ITAD company’s process networking equipment follows the NIST Clear standard. This is the only standard that has been available to them. Using the NIST clear, and manual deletion options has a high risk of missing user data and sending devices out with confidential customer data (i.e. passwords, customer names etc.).
There is a NIST Purge standard for network equipment, but this is vendor and product specific and does not lend itself to the objective of maximising the retained value of the asset as it will clear all software and licenses at the same time. If the ITAD is not careful, this may not be recoverable to an operational system and will result in loss of revenue for them. In time, this will then increase the costs of those services to you the disposal customer.
Processing Time
To process a device to NIST Purge can take time to ensure that all user data is cleared, depending on the device. This also requires a reasonable knowledge of networking hardware to either know the commands, or know how to get the commands.
Staff resource
The majority of companies that process their own networking equipment rely on a single member of staff, so when that person is absent no networking equipment is processed.
The Solution
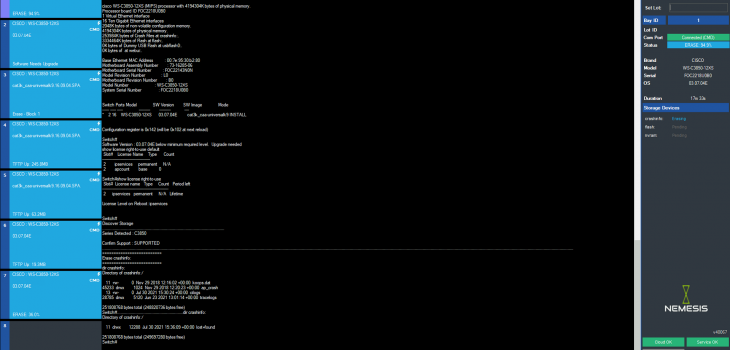
The new Nemesis Network Erasure product from Ultratest Solutions marks a revolutionary step forward in the processing of networking equipment collected by ITAD companies.
By utilising the Nemesis you gain the following:
- Simple to use, reliable and repeatable erasure process
Your Teams do not need to understand every device they are erasing. The solution detects the type of device, and processes it accordingly. It is just point and click.
- Allows erasure of products even if the OS has been deleted by the customer before the ITAD collected the devices.
- Utilises the VIP (Vendor Independent Purge) standard developed by Ultratest engineers to ensure that all data is fully erased.
- Confidence in providing erasure certificates that can be complimented by a full erasure report that can be provided to the customer.
- Maximise the value of any asset by bringing the device fully into an operation condition at the end of the erasure process.
To find out more, as to how Nemesis can benefit your operation, please get in contact and we will be happy to arrange a time for a consultative call to discuss your individual needs and challenges.







